

1. OpenShift 4.9 설치 및 환경구성
레드햇에서 유료로 제공중인 쿠버네티스의 상용화 버전, OpenShift (오픈시프트) 설치 방법입니다.
설치 시 진행한 서버 사양은 다음과 같습니다.
1-1. 설치 사양
| 서버명 | 호스트명 | IP 주소 | CPU Core | RAM | HDD |
| bastion | bastion.ocp4.rhocp.com | 192.168.100.11 | 8 Core | 16 GB | 150 GB |
| bootstrap | bootstrap.ocp4.rhocp.com | 192.168.100.12 | 2 Core | 8 GB | 150 GB |
| master1 | master1.ocp4.rhocp.com | 192.168.100.13 | 8 Core | 16 GB | 150 GB |
| worker1 | worker1.ocp4.rhocp.com | 192.168.100.14 | 8 Core | 16 GB | 150 GB |
| worker2 | worker2.ocp4.rhocp.com | 192.168.100.15 | 8 Core | 16 GB | 150 GB |
1-2. Bastion 설치
1) 편의성 패키지 설치
[root@bastion ~]# yum install tar wget
2) 호스트네임 설정
# hostnamectl set-hostname bastion.<cluster_name>.<base_domain>
[root@bastion ~]# hostnamectl set-hostname bastion.ocp4.rhocp.com
3) 방화벽 및 SELINUX 설정
[root@bastion ~]# vi /etc/selinux/config
...
SELINUX=disabled
[root@bastion ~]# systemctl disable firewalld --now
Removed /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service.
4) HAProxy 설치 및 구성, 시작
[root@bastion ~]# yum install haproxy
[root@bastion ~]# vi /etc/haproxy/haproxy.cfg
global
log 127.0.0.1 local2
chroot /var/lib/haproxy
pidfile /var/run/haproxy.pid
maxconn 4000
user haproxy
group haproxy
daemon
# turn on stats unix socket
stats socket /var/lib/haproxy/stats
# utilize system-wide crypto-policies
ssl-default-bind-ciphers PROFILE=SYSTEM
ssl-default-server-ciphers PROFILE=SYSTEM
defaults
mode http
log global
option httplog
option dontlognull
option http-server-close
option forwardfor except 127.0.0.0/8
option redispatch
retries 3
timeout http-request 10s
timeout queue 1m
timeout connect 10s
timeout client 1m
timeout server 1m
timeout http-keep-alive 10s
timeout check 10s
maxconn 3000
listen stats
bind :9000
mode http
stats enable
stats uri /
monitor-uri /bastion-test
stats refresh 5s
#---------------------------------------------------------------------
# static backend for serving up images, stylesheets and such
#---------------------------------------------------------------------
backend static
balance roundrobin
server static 127.0.0.1:4331 check
#---------------------------------------------------------------------
# RHOCP-API
#---------------------------------------------------------------------
frontend openshift-api-server
bind *:6443
default_backend openshift-api-server
mode tcp
option tcplog
backend openshift-api-server
balance source
mode tcp
server bootstrap 192.168.100.12:6443 check
server master1 192.168.100.13:6443 check
#---------------------------------------------------------------------
# RHOCP-machine-config-server
#---------------------------------------------------------------------
frontend machine-config-server
bind *:22623
default_backend machine-config-server
mode tcp
option tcplog
backend machine-config-server
balance source
mode tcp
server bootstrap 192.168.100.12:22623 check
server master1 192.168.100.13:22623 check
#---------------------------------------------------------------------
# RHOCP ingress-http (80)
#---------------------------------------------------------------------
frontend ingress-http
bind *:80
default_backend ingress-http
mode tcp
option tcplog
backend ingress-http
balance source
mode tcp
server worker1 192.168.100.14:80 check
server worker2 192.168.100.15:80 check
#---------------------------------------------------------------------
# RHOCP ingress-httpi (443)
#---------------------------------------------------------------------
frontend ingress-https
bind *:443
default_backend ingress-https
mode tcp
option tcplog
backend ingress-https
balance source
mode tcp
server worker1 192.168.100.14:443 check
server worker2 192.168.100.15:443 check
[root@bastion ~]# systemctl enable haproxy --now
5) HTTP 서버 설치 및 구성, 시작
[root@bastion ~]# yum install httpd
[root@bastion ~]# vi /etc/httpd/conf/httpd.conf
# Listen: Allows you to bind Apache to specific IP addresses and/or
# Change this to Listen on specific IP addresses as shown below to
#Listen 12.34.56.78:80
Listen 8080
6) DNS 서버 설치 및 구성, 시작
- /etc/named.conf 수정
[root@bastion ~]# vi /etc/named.conf
options {
listen-on port 53 { any; };
listen-on-v6 port 53 { none; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { any; };
- /etc/named.rfc1912.zones 수정
[root@bastion ~]# vi /etc/named.rfc1912.zones
...
zone "rhocp.com" IN {
type master;
file "/var/named/ocp4.rhocp.com.zone";
allow-update { none; };
};
zone "100.168.192.in-addr.arpa" IN {
type master;
file "/var/named/rev.ocp4.rhocp.com";
allow-update { none; };
};
- zone 파일 설정 (DNS 정방향)
[root@bastion ~]# vi /var/named/ocp4.rhocp.com.zone
$TTL 1D
@ IN SOA @ ns.rhocp.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
@ IN NS ns.rhocp.com.
@ IN A 192.168.100.11 ;
; Ancillary services
lb.ocp4 IN A 192.168.100.11
; Bastion or Jumphost
ns IN A 192.168.100.11 ;
; OCP Cluster
bootstrap.ocp4 IN A 192.168.100.12
master1.ocp4 IN A 192.168.100.13
worker1.ocp4 IN A 192.168.100.14
worker2.ocp4 IN A 192.168.100.15
api.ocp4 IN A 192.168.100.11
api-int.ocp4 IN A 192.168.100.11
*.apps.ocp4 IN A 192.168.100.11
apps.ocp4 IN A 192.168.100.11
console-openshift-console.apps.ocp4.rhocp.com. IN A 192.168.100.11
oauth-openshift.apps.ocp4.rhocp.com. IN A 192.168.100.11
- zone 파일 설정 (DNS 역방향)
[root@bastion ~]# vi /var/named/rev.ocp4.rhocp.com
$TTL 1D
@ IN SOA rhocp.com. ns.rhocp.com. (
0 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
@ IN NS ns.
11 IN PTR ns.
11 IN PTR bastion.ocp4.rhocp.com.
12 IN PTR bootstrap.ocp4.rhocp.com.
13 IN PTR master1.ocp4.rhocp.com.
14 IN PTR worker1.ocp4.rhocp.com.
15 IN PTR worker2.ocp4.rhocp.com.
11 IN PTR api.ocp4.rhocp.com.
11 IN PTR api-int.ocp4.rhocp.com.
- zone 파일 권한 수정
[root@bastion named]# chown root.named ocp4.rhocp.com.zone rev.ocp4.rhocp.com
- DNS 서버 시작
[root@bastion named]# chown root.named ocp4.rhocp.com.zone rev.ocp4.rhocp.com
1-3. OpenShift 4.9 배포 준비
OpenShift 4.9 배포는 openshift-install을 이용하여 진행합니다.
각 노드들에 맞는 ignition 파일을 생성해서 http 웹서버에서 서비스가 되도록 설정해줍니다.
1) ssh-key 생성
[root@bastion ~]# ssh-keygen -t rsa -b 4096 -N ''
2) openshift-client, openshift-install 바이너리 다운로드
[root@bastion ~]# mkdir -p ~/openshift/config
[root@bastion ~]# mkdir -p ~/install
[root@bastion ~]# cd ~/install
[root@bastion install]# wget https://mirror.openshift.com/pub/openshift-v4/clients/ocp/4.9.0/openshift-client-linux-4.9.0.tar.gz
[root@bastion install]# wget https://mirror.openshift.com/pub/openshift-v4/clients/ocp/4.9.0/openshift-install-linux-4.9.0.tar.gz
[root@bastion install]# tar -zxvf openshift-client-linux-4.9.0.tar.gz
[root@bastion install]# tar -zxvf openshift-install-linux-4.9.0.tar.gz
[root@bastion install]# rm -rf README.rd
[root@bastion install]# mv kubectl oc openshift-install /usr/bin/
3) install-config.yaml 파일 생성 및 백업
[root@bastion ~]# mkdir -p ~/openshift/backup
[root@bastion backup]# cd ~/openshift/backup
[root@bastion backup]# vi install-config.yamlapiVersion: v1
baseDomain: rhocp.com
compute:
- hyperthreading: Enabled
name: worker
replicas: 0
controlPlane:
hyperthreading: Enabled
name: master
replicas: 1
metadata:
name: ocp4
networking:
clusterNetwork:
- cidr: 10.128.0.0/14
hostPrefix: 23
networkType: OVNKubernetes
serviceNetwork:
- 172.30.0.0/16
platform:
none: {}
fips: false
pullSecret: '<pullSecret값 추가>'
sshKey: '<ssh-key값 추가>'
# pulsect : https://console.redhat.com/openshift/create
# sshKey -> cat /root/,ssh/id_rsa.pub 값을 추가[root@bastion backup]# cp install-config.yaml ../config/
1-4. manifests 및 ignition 파일 생성
openshift-install 바이너리를 이용하여 OCP Cluster 설치를 위한 manifests와 ignition 파일을 생성합니다.
1) manifests 파일 생성
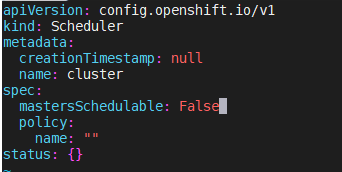
manifests를 설치한 후, manifests 폴더의 cluster-scheduler-02-config.yml 를 수정합니다.
mastersSchedulable을 true 인 경우 master node의 role은 master, worker 로 부여되며
false로 수정할 경우 master role 만 부여됩니다.
[root@bastion config]# openshift-install create manifests --dir=/root/openshift/config/
INFO Consuming Install Config from target directory
WARNING Making control-plane schedulable by setting MastersSchedulable to true for Scheduler cluster settings
INFO Manifests created in: /root/openshift/config/manifests and /root/openshift/config/openshift
# mastersSchedulable 값을 true 에서 false로 변경
[root@bastion config]# cd manifests
[root@bastion manifests]# vi cluster-scheduler-02-config.yml
...
spec:
mastersSchedulable: false
...
2) ignition 파일 생성
[root@bastion config]# openshift-install create ignition-configs --dir=/root/openshift/config/
INFO Consuming Master Machines from target directory
INFO Consuming Worker Machines from target directory
INFO Consuming Common Manifests from target directory
INFO Consuming Openshift Manifests from target directory
INFO Consuming OpenShift Install (Manifests) from target directory
INFO Ignition-Configs created in: /root/openshift/config and /root/openshift/config/auth
[root@bastion config]# mkdir -p /var/www/html/ign
[root@bastion config]# cp *.ign /var/www/html/ign/
[root@bastion config]# chmod 777 /var/www/html/ign/*.ign
[root@bastion config]# systemctl restart httpd
2. OpenShift 4.9 배포
2-1. Bootstrap 생성
CoreOS를 설치하기 위해 RHCOS 4.9 (rhcos-4.9.0-live.x86_64.iso) iso 파일로 부팅하여 설치합니다.
1) 호스트네임 및 네트워크 설정
[core@localhost ~]# sudo -i
[root@localhost ~]# hostnamectl set-hostname bootstrap.ocp4.rhocp.com
[root@bootstrap ~]# nmcli con add con-name ens3 type ethernet ifname ens3 ipv4.method manual \
ipv4.address 192.168.100.12/24 \
ipv4.gateway 192.168.100.1 \
ipv4.dns 192.168.100.12 \
connection.autoconnect yes
[root@bootstrap ~]# nmcli con up ens3
[root@bootstrap ~]# nmcli con del 'Wired connection 1'
[root@bootstrap ~]# nmcli con
[root@bootstrap ~]# ifconfig
[root@bootstrap ~]# cat /etc/resolv.conf
nameserver 192.168.100.11
2) Bootstrap 설치 후 reboot
[core@bootstrap ~]# sudo coreos-installer install /dev/sda --insecure-ignition \
-I http://192.168.100.11:8080/ign/bootstrap.ign -n
install complete.
[core@bootstrap ~]# sudo reboot
3) Bootstrap 설치 완료 확인
[root@bastion ~]# openshift-install --dir=/root/openshift/config wait-for bootstrap-complete --log-level=info
INFO Waiting up to 20m0s for the Kubernetes API at https://api.ocp4.rhocp.com:6443...
INFO API v1.21.1+a620f50 up
INFO Waiting up to 30m0s for bootstrapping to complete...위 로그가 정상적으로 출력된다면 이제 master 노드 설치를 진행할 수 있습니다. (시간이 좀 걸릴수 있습니다.)
2-2. master 노드 설치
bootstrap 설치한 방식과 동일하게 master 노드를 설치합니다.
1) 호스트네임 및 네트워크 설정
[core@localhost ~]# sudo -i
[root@localhost ~]# hostnamectl set-hostname master1.ocp4.rhocp.com
[root@master1 ~]# nmcli con add ens3 type ethernet ifname ens3 ipv4.method manual \
ipv4.address 192.168.100.13/24 \
ipv4.gateway 192.168.100.1 \
ipv4.dns 192.168.100.11 \
connection.autoconnect yes
[root@master1 ~]# nmcli con up ens3
[root@master1 ~]# nmcli con del 'Wired connection 1'
[root@master1 ~]# nmcli con
[root@master1 ~]# ifconfig
[root@master1 ~]# cat /etc/resolv.conf
nameserver 192.168.100.11
2) master 설치 후 reboot
[core@master1 ~]# sudo coreos-installer install /dev/sda --insecure-ignition \
-I http://192.168.100.11:8080/ign/master.ign -n
install complete.
[core@master1 ~]# sudo reboot
3) master 노드 구성 확인
master 노드를 모두 설치하였다면, Bastion에서 아래와 같은 로그가 출력되는지 확인합니다.
아래 로그의 의미는 Bootstrap 노드를 이용하여 Master 노드의 클러스터링이 완료되었으므로, Bootstrap 노드는 더이상 필요하지 않다는 의미입니다.
[root@bastion ~]# openshift-install --dir=/root/openshift/config wait-for bootstrap-complete --log-level=info
INFO Waiting up to 20m0s for the Kubernetes API at https://api.ocp4.rhocp.com:6443...
INFO API v1.21.1+a620f50 up
INFO Waiting up to 30m0s for bootstrapping to complete...
INFO It is now safe to remove the bootstrap resources
INFO Time elapsed: 0s
4) HAProxy 설정 변경
OpenShift 클러스터가 정상적으로 구성되었기 때문에, HAProxy에서 bootstrap으로 LB되지 않도록 수정 후, 서비스를 재시작합니다.
[root@bastion ~]# vi /etc/haproxy/haproxy.cfg
...
backend openshift-api-server
balance source
mode tcp
#server bootstrap 192.168.100.12:6443 check
server master1 192.168.100.13:6443 check
backend machine-config-server
balance source
mode tcp
#server bootstrap 192.168.100.12:22623 check
server master1 192.168.100.13:22623 check
[root@bastion ~]# systemctl restart haproxy
3. OpenShift 4.9 로그인 및 확인
3-1. OpenShift 노드 정보 확인
1) kubeadmin export 설정
[root@bastion ~]# cat ~/.bash_profile
...
export KUBECONFIG=/root/openshift/config/auth/kubeconfig
2) 노드 정보 확인
[root@bastion ~]# oc get node
NAME STATUS ROLES AGE VERSION
master1.ocp4.rhocp.com Ready master 33m v1.21.1+a620f50
3) OpenShift Cluster Component 동작 확인
모든 Cluster Operator가 True / False / False 로 출력되어야 정상입니다.
[root@bastion ~]# oc get co
NAME VERSION AVAILABLE PROGRESSING DEGRADED SINCE
authentication 4.9.0 True False False 24m
baremetal 4.9.0 True False False 4m3s
cloud-credential 4.9.0 True False False 44m
cluster-autoscaler 4.9.0 True False False 17m
config-operator 4.9.0 True False False 23m
console 4.9.0 True False False 19s
csi-snapshot-controller 4.9.0 True False False 3m22s
dns 4.9.0 True False False 7m27s
etcd 4.9.0 True False False 17m
image-registry 4.9.0 True False False 2s
ingress
insights 4.9.0 True False False 15m
kube-apiserver 4.9.0 True False False 2m
kube-controller-manager 4.9.0 True False False 19m
kube-scheduler 4.9.0 True False False 18m
kube-storage-version-migrator 4.9.0 True False False 11m
machine-api 4.9.0 True False False 15m
machine-approver 4.9.0 True False False 19m
machine-config 4.9.0 True False False 7m1s
marketplace 4.9.0 True False False 15m
monitoring True False False 18m
network 4.9.0 True False False 26m
node-tuning 4.9.0 True False False 8m52s
openshift-apiserver 4.9.0 True False False 31s
openshift-controller-manager 4.9.0 True False False 4m42s
openshift-samples
operator-lifecycle-manager 4.9.0 True False False 15m
operator-lifecycle-manager-catalog 4.9.0 True False False 15m
operator-lifecycle-manager-packageserver 4.9.0 True False False 3m33s
service-ca 4.9.0 True False False 24m
storage 4.9.0 True False False 23m
4) OpenShift 4.9 Cluster 설치 완료 확인
[root@bastion ~]# openshift-install --dir=/root/openshift/config wait-for install-complete
INFO Waiting up to 40m0s for the cluster at https://api.ocp4.rhocp.com:6443 to initialize...
INFO Waiting up to 10m0s for the openshift-console route to be created...
INFO Install complete!
INFO To access the cluster as the system:admin user when using 'oc', run 'export KUBECONFIG=/root/openshift-4.8/config/auth/kubeconfig'
INFO Access the OpenShift web-console here: https://console-openshift-console.apps.ocp4.rhocp.com
INFO Login to the console with user: "kubeadmin", and password: "xxxxxxxxx"
INFO Time elapsed: 0s
4. worker 노드 추가
master 노드 설치 후 클러스터 구성이 완료되면, worker 노드를 수동으로 추가해줍니다.
4-1. worker1 노드 설치
1) 호스트네임 및 네트워크 설정
[core@localhost ~]# sudo -i
[root@localhost ~]# hostnamectl set-hostname worker1.ocp4.rhocp.com
[root@worker1 ~]# nmcli con add ens3 type ethernet ifname ens3 ipv4.method manual \
ipv4.address 192.168.100.14/24 \
ipv4.gateway 192.168.100.1 \
ipv4.dns 192.168.100.11 \
connection.autoconnect yes
[root@worker1 ~]# nmcli con up ens3
[root@worker1 ~]# nmcli con del 'Wired connection 1'
[root@worker1 ~]# nmcli con
[root@worker1 ~]# ifconfig
[root@worker1 ~]# cat /etc/resolv.conf
nameserver 192.168.100.11
2) worker1 설치 후 reboot
[core@worker1 ~]# sudo coreos-installer install /dev/sda --insecure-ignition \
-I http://192.168.100.11:8080/ign/worker.ign -n
install complete.
[core@worker1 ~]# sudo reboot
4-2. worker2 노드 설치
1) 호스트네임 및 네트워크 설정
[core@localhost ~]# sudo -i
[root@localhost ~]# hostnamectl set-hostname worker1.ocp4.rhocp.com
[root@worker1 ~]# nmcli con add ens3 type ethernet ifname ens3 ipv4.method manual \
ipv4.address 192.168.100.15/24 \
ipv4.gateway 192.168.100.1 \
ipv4.dns 192.168.100.11 \
connection.autoconnect yes
[root@worker1 ~]# nmcli con up ens3
[root@worker1 ~]# nmcli con del 'Wired connection 1'
[root@worker1 ~]# nmcli con
[root@worker1 ~]# ifconfig
[root@worker1 ~]# cat /etc/resolv.conf
nameserver 192.168.100.11
2) worker1 설치 후 reboot
[core@worker1 ~]# sudo coreos-installer install /dev/sda --insecure-ignition \
-I http://192.168.100.11:8080/ign/worker.ign -n
install complete.
[core@worker1 ~]# sudo reboot
4-3. worker 노드 인증 승인 (csr)
1) csr 확인 및 승인
pending 상태인 csr을 approve 시켜줍니다.
[root@bastion ~]# oc get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-kv9mp 3m21s kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Pending
csr-m2xf2 62m kubernetes.io/kubelet-serving system:node:master1.ocp4.rhocp.com Approved,Issued
csr-nf5wh 62m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Approved,Issued
system:openshift:openshift-authenticator 49m kubernetes.io/kube-apiserver-client system:serviceaccount:openshift-authentication-operator:authentication-operator Approved,Issued
[root@bastion ~]# oc adm certificate approve csr-kv9mp
certificatesigningrequest.certificates.k8s.io/csr-kv9mp approved
[root@bastion ~]# oc get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-ck6c6 7s kubernetes.io/kubelet-serving system:node:worker1.ocp4.rhocp.com Pending
csr-kv9mp 4m30s kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Approved,Issued
csr-m2xf2 63m kubernetes.io/kubelet-serving system:node:master1.ocp4.rhocp.com Approved,Issued
csr-nf5wh 64m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Approved,Issued
system:openshift:openshift-authenticator 50m kubernetes.io/kube-apiserver-client system:serviceaccount:openshift-authentication-operator:authentication-operator Approved,Issued
[root@bastion ~]# oc adm certificate approve csr-ck6c6
certificatesigningrequest.certificates.k8s.io/csr-ck6c6 approved
[root@bastion ~]# oc get csr
NAME AGE SIGNERNAME REQUESTOR CONDITION
csr-ck6c6 72s kubernetes.io/kubelet-serving system:node:worker1.ocp4.rhocp.com Approved,Issued
csr-kv9mp 5m35s kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Approved,Issued
csr-m2xf2 64m kubernetes.io/kubelet-serving system:node:master1.ocp4.rhocp.com Approved,Issued
csr-nf5wh 65m kubernetes.io/kube-apiserver-client-kubelet system:serviceaccount:openshift-machine-config-operator:node-bootstrapper Approved,Issued
system:openshift:openshift-authenticator 51m kubernetes.io/kube-apiserver-client system:serviceaccount:openshift-authentication-operator:authentication-operator Approved,Issued
2) 노드 정보 확인
[root@bastion ~]# oc get node
NAME STATUS ROLES AGE VERSION
master1.ocp4.rhocp.com Ready master 33m v1.21.1+a620f50
worker1.ocp4.rhocp.com Ready worker 15m v1.21.1+a620f50
worker2.ocp4.rhocp.com Ready worker 11m v1.21.1+a620f50
3) OpenShift Cluster Component 동작 확인
모든 Cluster Operator가 True / False / False 로 출력되어야 정상입니다.
[root@bastion ~]# oc get co
NAME VERSION AVAILABLE PROGRESSING DEGRADED SINCE
authentication 4.9.0 True False False 24m
baremetal 4.9.0 True False False 4m3s
cloud-credential 4.9.0 True False False 44m
cluster-autoscaler 4.9.0 True False False 17m
config-operator 4.9.0 True False False 23m
console 4.9.0 True False False 19s
csi-snapshot-controller 4.9.0 True False False 3m22s
dns 4.9.0 True False False 7m27s
etcd 4.9.0 True False False 17m
image-registry 4.9.0 True False False 2s
ingress
insights 4.9.0 True False False 15m
kube-apiserver 4.9.0 True False False 2m
kube-controller-manager 4.9.0 True False False 19m
kube-scheduler 4.9.0 True False False 18m
kube-storage-version-migrator 4.9.0 True False False 11m
machine-api 4.9.0 True False False 15m
machine-approver 4.9.0 True False False 19m
machine-config 4.9.0 True False False 7m1s
marketplace 4.9.0 True False False 15m
monitoring True False False 18m
network 4.9.0 True False False 26m
node-tuning 4.9.0 True False False 8m52s
openshift-apiserver 4.9.0 True False False 31s
openshift-controller-manager 4.9.0 True False False 4m42s
openshift-samples
operator-lifecycle-manager 4.9.0 True False False 15m
operator-lifecycle-manager-catalog 4.9.0 True False False 15m
operator-lifecycle-manager-packageserver 4.9.0 True False False 3m33s
service-ca 4.9.0 True False False 24m
storage 4.9.0 True False False 23m